Turbocharge Security with Multi Factor Consultation Blueprint Now
Turbocharge your organization's security with a Multi-Factor Authentication (MFA) Consultation Blueprint and discover how you can effectively shield sensitive data while exploring the latest options in cybersecurity solutions.
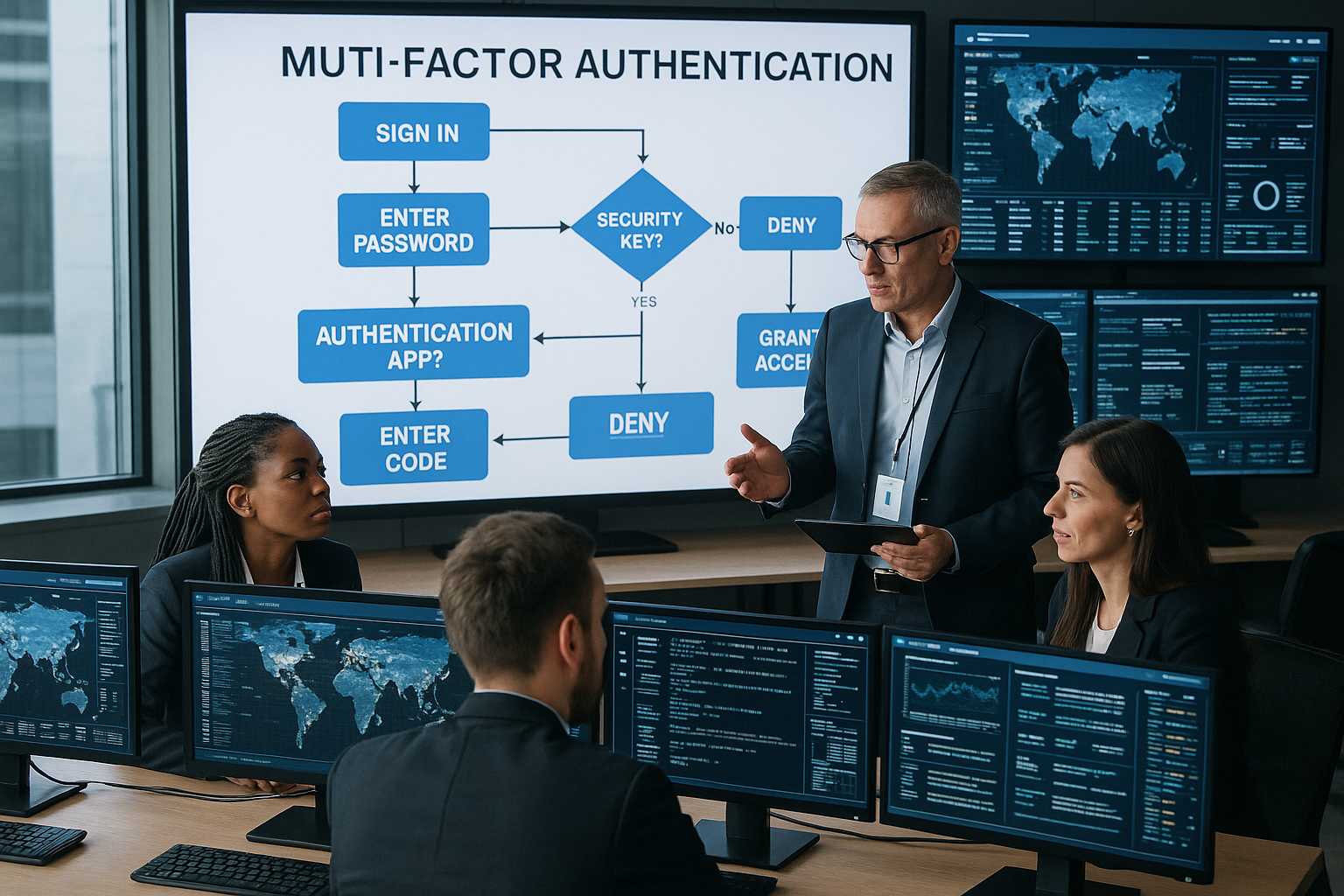
Understanding Multi-Factor Authentication (MFA)
Multi-Factor Authentication (MFA) is a security system that requires more than one method of authentication to verify a user's identity. This typically includes something you know (a password), something you have (a smartphone or hardware token), and something you are (biometric verification like a fingerprint). MFA adds an extra layer of protection beyond just passwords, which can be easily compromised. By implementing MFA, businesses can significantly reduce the risk of unauthorized access and data breaches.
The Importance of an MFA Consultation Blueprint
An MFA Consultation Blueprint is a strategic plan that outlines the steps necessary to implement and optimize MFA within an organization. This blueprint not only guides IT teams through the technical setup but also addresses user adoption and policy management. By following a well-structured blueprint, companies can ensure a seamless transition to enhanced security measures. Moreover, this approach helps in identifying the specific needs of the organization, thereby customizing the MFA setup for maximum efficiency and cost-effectiveness.
Benefits of Implementing MFA
1. **Enhanced Security**: MFA provides an additional layer of security, making it significantly harder for attackers to gain unauthorized access. According to a study by Microsoft, MFA can block over 99.9% of account compromise attacks1.
2. **Compliance and Risk Management**: Many regulatory frameworks require the use of MFA to protect sensitive information. Implementing MFA helps organizations comply with standards such as GDPR, HIPAA, and PCI-DSS, reducing the risk of legal penalties2.
3. **User Experience**: While adding extra steps might seem cumbersome, modern MFA solutions are designed to be user-friendly. With options like push notifications and biometric logins, users can enjoy a smoother authentication process without compromising on security.
Cost Considerations and ROI
While the initial investment in MFA solutions might seem significant, the return on investment is substantial. The cost of a data breach can be astronomical, with the average breach costing companies $3.86 million globally3. By preventing breaches, MFA solutions can save organizations from these potential losses. Additionally, many MFA providers offer scalable solutions, allowing businesses to choose plans that fit their budget and scale as they grow.
Exploring MFA Solutions
To effectively implement MFA, organizations should start by browsing options from reputable providers. Popular solutions include Microsoft Azure MFA, Google Authenticator, and Duo Security, each offering unique features tailored to different business needs. By visiting websites and exploring these options, businesses can find the right solution that aligns with their security requirements and budget constraints.
Real-World Examples
Many organizations have successfully implemented MFA to enhance their security posture. For instance, the University of California, Berkeley, deployed an MFA solution that resulted in a 90% reduction in compromised accounts4. Such examples demonstrate the tangible benefits of investing in a robust MFA system.
By adopting a Multi-Factor Authentication Consultation Blueprint, you can fortify your organization’s defenses against cyber threats while ensuring compliance and enhancing user experience. As you search options and explore the latest in cybersecurity, consider the long-term benefits and peace of mind that a well-implemented MFA strategy can provide.